Integrating with Active Directory Federation Services (ADFS)
If you have Active Directory Federation Services configured in your environment, you can use it to manage Tripwire.io authentication.
Once ADFS integration is configured, users who log in to Tripwire.io with an email address from your domain will be redirected to your ADFS server login page. After they enter their AD credentials, they will be taken back to Tripwire.io. If a user is already logged in to your domain, they will not be prompted for a password at all.
Before you can create an Identity Provider in Tripwire.io, you need the following pieces of information from your ADFS server:
the Issuer URI or EntityID of your ADFS server
the SSO URL of your ADFS server
the PEM-encoded public key certificate of your ADFS server
To find the Issuer URI or EntityID of your ADFS server:
| 1. | Download the FederationMetadata.xml file from the Endpoints section of your ADFS Management tool. |
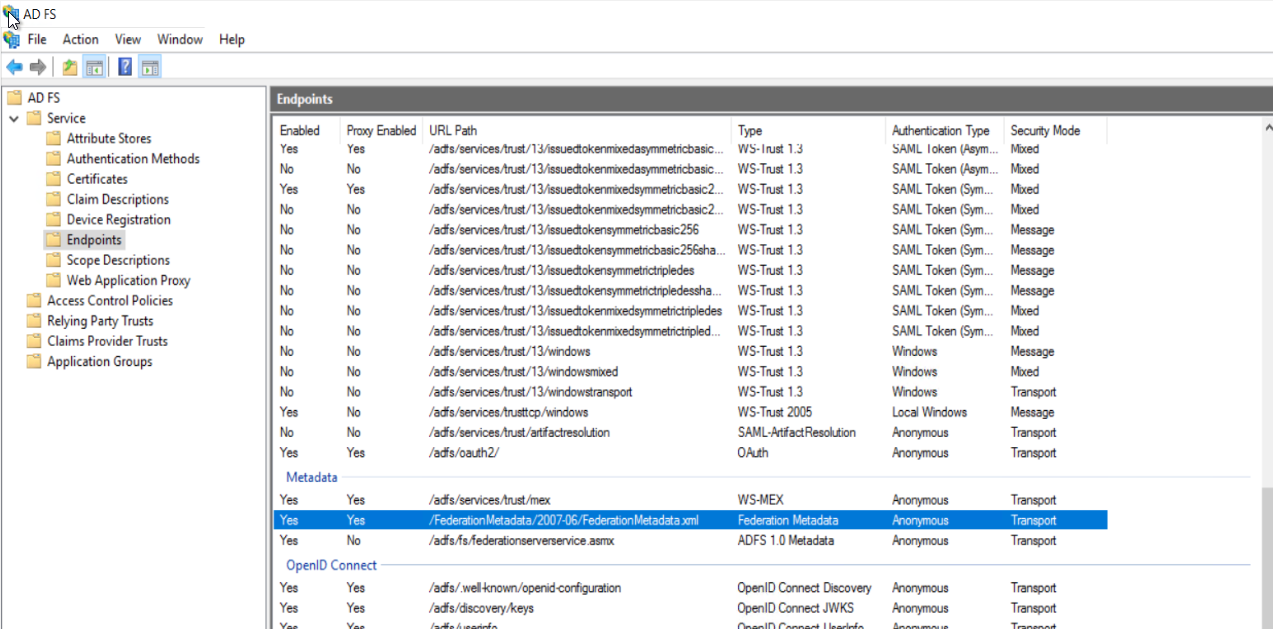
| 2. | Open the FederationMetadata.xml file and find the entityID section for the Issuer URI. The default Issuer URI will look like http://{yourdomain}/adfs/services/trust. |

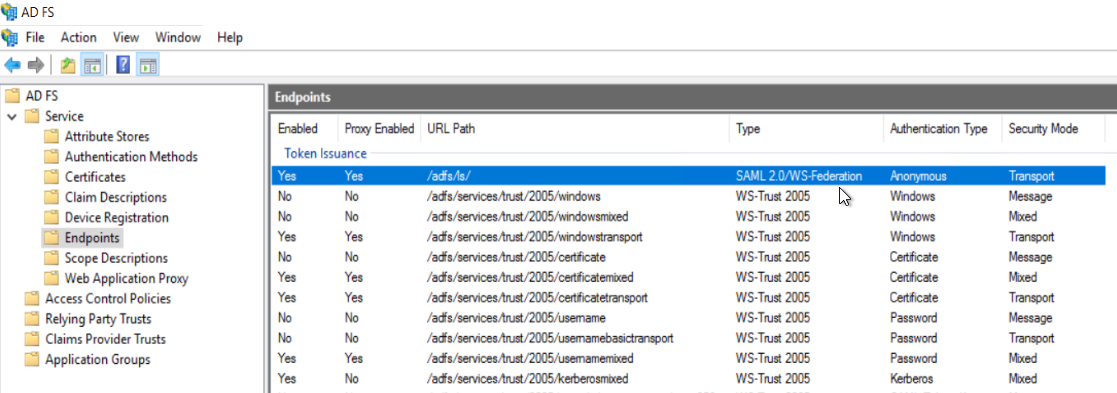
To find the SSO URL of your ADFS server:
Look in the Endpoints section of the ADFS Management tool. The default SSO URL of your ADFS server will look like https://{yourdomain}/adfs/ls.
To find the PEM-encoded public key certificate of your ADFS server:
| 1. | Open the ADFS Management program, expand Service and then click Certificates. |
| 2. | Right click on the Token-signing value and select View Certificate. |
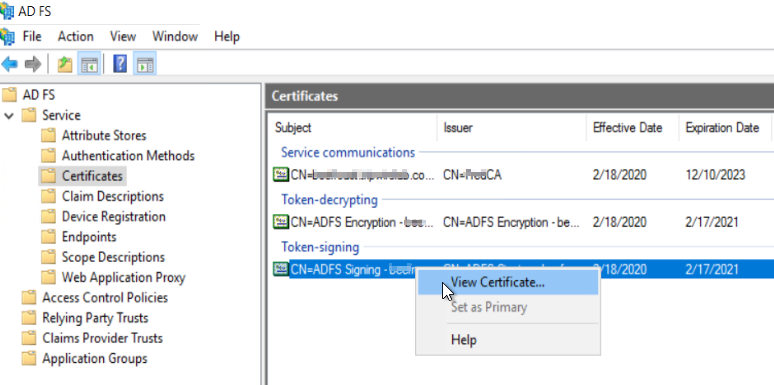
| 3. | In the Certificate dialog, select the Details tab, then click Copy to File. |
| 4. | In the Certificate Export Wizard, select Base-64 encoded X.509 (.CER). |
With the information from your ADFS server, you can create the Identity Provider in Tripwire.io.
| 1. | Log in to Tripwire.io as a user with the CustomerAdmin role and navigate to Settings > User Management. |
| 2. | Select the Identity Providers tab. |
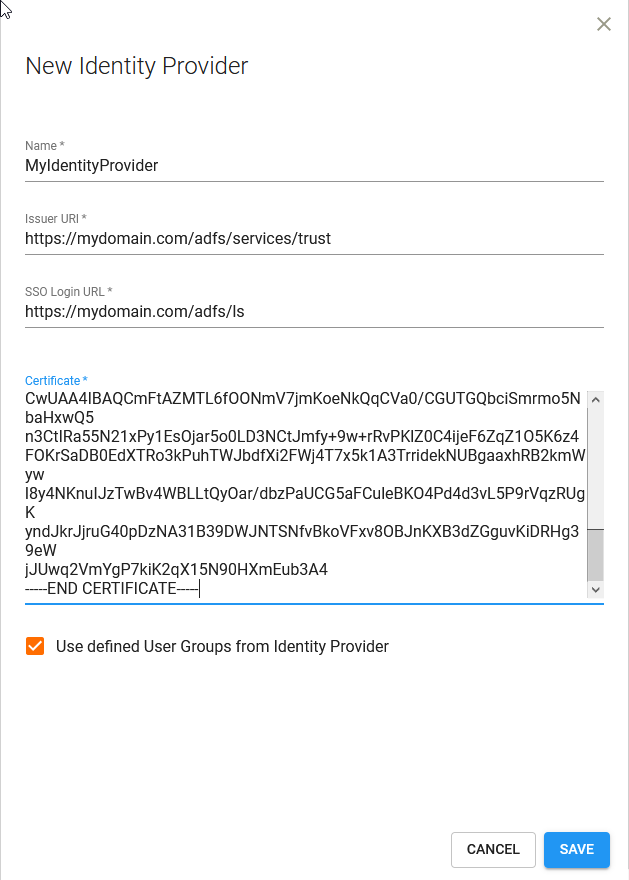
| 3. | Click Add Identity Provider and fill out the fields in the New Identity Provider pane, using the information you gathered in the previous step. Paste the content of the public key certificate into the Certificate field. |
Select Use defined User Groups from Identity Provider if you want to manage Tripwire.io group membership from your ADFS server.
|
Note: |
If you change the certificate on your ADFS server, you must also update the certificate information here to match. |
|---|
| 4. | Click Save when finished. |
| 5. | When the new Identity Provider appears in the list, click it. |
| 6. | In the View Identity Provider pane, click Metadata.xml to download a SAML2 metadata file for the next step. |
You can now add a Relying Party Trust in your ADFS Management tool.
| 1. | In your ADFS Management tool, select Relying Party Trusts and Add Relying Party Trust. |
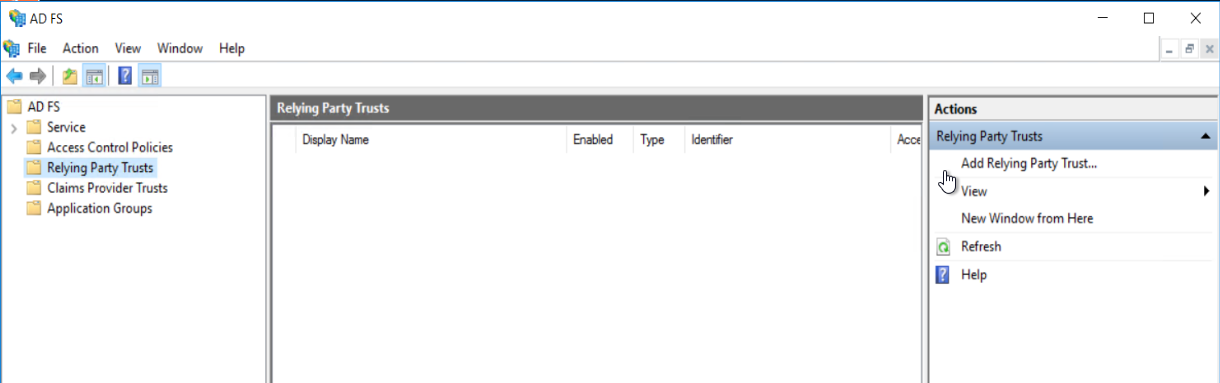
| 2. | Create a Claims aware Relying Party Trust and import the metadata.xml file from the previous step. |
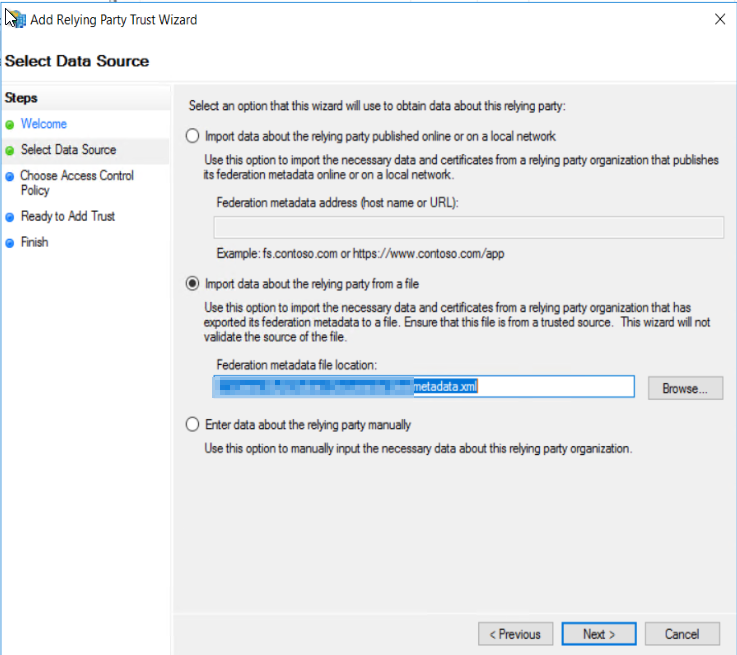
| 3. | In the Relying Party Trust Wizard, you can initially set the access control policy to permit access to anyone, or limit it to a specific AD group. |
|
Note: |
To change the access control policy for your relying party trust later, select it in the ADFS Management tool and click Edit Access Control Policy. |
|---|
| 4. | Complete the wizard. |
Next you will add a Claim Issuance Policy, which includes the minimum LDAP attributes mapped in the claim.
| 1. | Select the relying party trust you just created. |
| 2. | Click Edit Claim Issuance Policy and Add Rule. |
| 3. | In the Add Transform Claim Rule Wizard, select Send LDAP Attributes as Claims and click Next. |

| 4. | Select Active Directory from the Attribute Store, map the attributes below, then apply your changes. |
|
LDAP Attribute |
Outgoing Claim Type |
|---|---|
|
E-Mail-Addresses |
E-Mail Address |
|
Given-Name |
Given Name |
|
Surname |
Surname |
|
User-Principal-Name |
Name ID |
Next add your domain to your identity provider and verify it by adding a DNS text record.
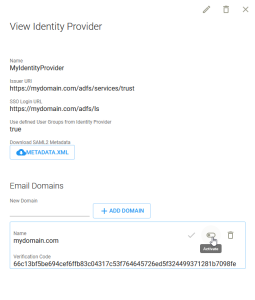
| 1. | In Tripwire.io, navigate to Settings > User Management > Identity Providers and select the identity provider you created for the ADFS integration. |
| 2. | In the View Identity Provider pane, enter your domain under New Domain and click Add Domain. Your domain is added and displays a verification code. |

| 3. | In your domain's DNS zone editor, add a text record with the following name: |
'_tripwire_io_verification.{domain_name}'
For the record value, use the verification code from the previous step. For example:
_tripwire_io_verification.mydomain.com 66c13bf5be694cef6ffb83c04317c53f764645726ed5f324499371281b7098fe
| 4. | In the Tripwire.io View Identity Provider pane, click Verify to verify your domain. |
Next you need to designate at least one Tripwire.io user account that is authenticated by Tripwire.io and not controlled by your identity provider (an "Internal" account). This account can be used if your ADFS server has problems and you need to access Tripwire.io.
| 1. | In Tripwire.io, navigate to Settings > User Management > Users. |
| 2. | Select the user account you want to make an internal account (or create a new one) and click Edit. |
|
Note: |
The user account that you select must have the CustomerAdmin role. |
|---|
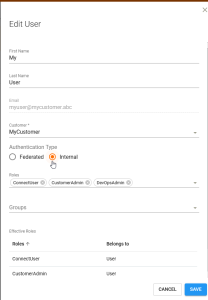
| 3. | In the Edit User dialog, select Internal as the Authentication Type and click Save. |
|
Note: |
If you change a Federated user to an Internal user after activating your identity provider, Tripwire.io will send them an activation email to create local credentials. If you change an Internal user to a Federated user, Tripwire.io will delete their local password, recovery questions, and multi-factor authentication factors. |
|---|
Now activate your domain in your identity provider to authenticate all users from your domain using your ADFS server.
| 1. | In Tripwire.io, navigate to Settings > User Management > Identity Providers and select the identity provider you created for the ADFS integration. |
| 2. | In the View Identity Provider pane, click Activate to activate your domain. |
To deactivate your identity provider in the future, click Deactivate. If you deactivate your identity provider, Tripwire.io will send all users an activation email to create local credentials.
In addition to authentication, you can also use Active Directory to manage Tripwire.io group membership. If configured, Tripwire.io users that are authenticated using Active Directory will be assigned to Tripwire.io User Groups (with corresponding roles) based on their AD group membership.
| 1. | In Tripwire.io, navigate to Settings > User Management > User Groups. |
|
Note: |
You will need the CustomerAdmin role to create groups. |
|---|
| 2. | Click New Group and complete the New User Group form: |
| a. | Enter a Group Name and select the Roles to be applied to group members. Leave the other fields blank. |
| b. | Click Save. |
| 3. | On the User Groups page, click the Group Name of the group you just created to see more details and then copy the Group ID. |
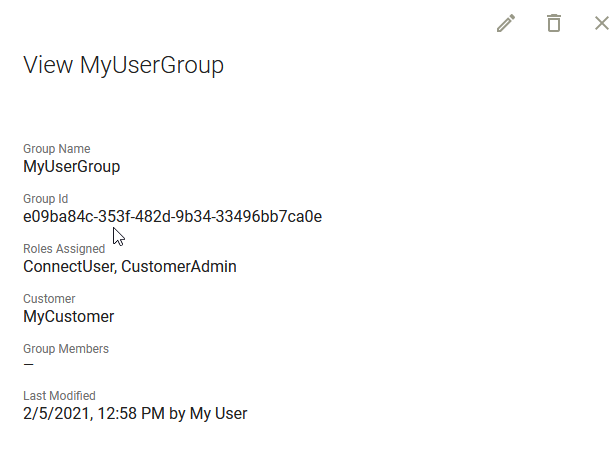
| 4. | In your ADFS Management tool, select your relying party trust and then Edit Claim Issuance Policy. |
| 5. | Now create a Claim Issuance Policy rule for the AD group you want to map to the Tripwire.io User Group: |
| a. | Click Add Rule. |
| b. | In the Add Transform Claim Rule Wizard select Send Group Membership as Claims and click Next. |

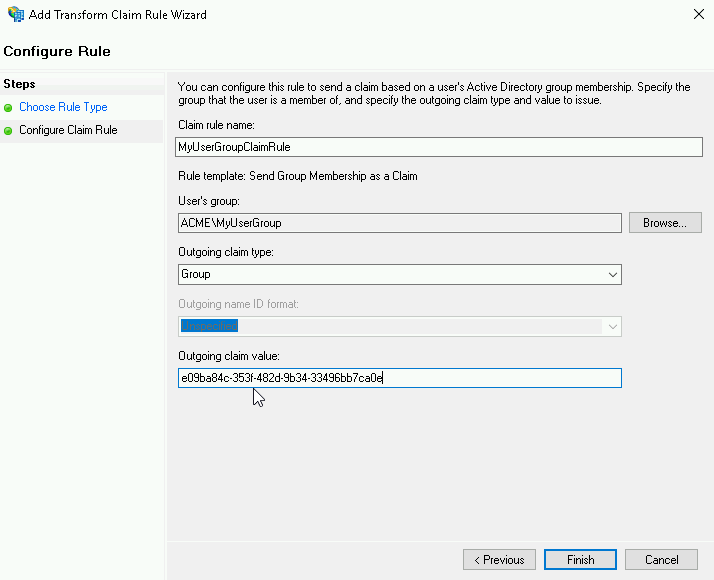
| 6. | On the Configure Claim Rule page: |
| a. | For User's group, enter or select the AD group you want to map. |
| b. | For Outgoing claim type, select Group. |
| c. | For Outgoing claim value, paste the Tripwire.io Group ID you copied earlier. |
| d. | Click Finish to apply the change to your claims issuance policy. |
Repeat this process for each AD group that you want to map to a Tripwire.io group.
Log out of Tripwire.io and then log back in to test the configuration.
When users log in to Tripwire.io with an email address from your domain, they should be redirected to your ADFS server login page. After they enter their AD credentials, they will be taken back to Tripwire.io. If the user is already logged in to your domain, they should not be prompted for a password at all.
If you configured group mappings in Step 8: (Optional) Configure User Group Mappings, make sure that AD group membership is correctly reflected in your Tripwire.io groups.