Creating an AWS External (with EKS) Cloud Account
A Cloud Account is a cloud environment that Configuration Manager monitors. For more information about monitoring Cloud Accounts, see Getting Started with Configuration Manager.
The AWS External (with EKS) account type uses a role in the customer's AWS account that grants Tripwire.io permission to assume the role directly. For more information on how this role type works, see the AWS documentation on External ID.
Quick Start Video
This video provides a simplified overview of the procedure below.
Since this role requires some information from Tripwire.io, the simplest way to create the role is to use our "Launch Stack" CloudFormation template, which populates all of this information.
|
Tip: |
An AWS External (with EKS) account is identical to a standard AWS External account but requires additional configuration to support scanning of an EKS cluster. You can re-use the Role ARN value from an existing AWS External account if you want to create a separate Configuration Manager account for scanning EKS clusters. |
|---|
-
In Configuration Manager, navigate to Environment > Cloud Accounts and click New.
-
In the New Cloud Account pane, enter a Name and Description to identify this account.
-
Select AWS External (with EKS) as the account Type and select a Region.
-
To enable Configuration Manager to remediate systems on this account, check Include write permissions for remediation. Otherwise, CM will only have read-only access.
-
Click Launch Stack to open the CloudFormation template in the AWS console (after signing in).
Do not close the Tripwire.io tab/window.
-
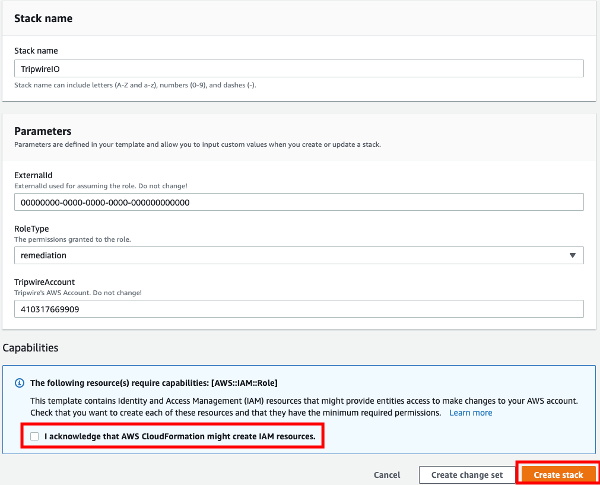
On the CloudFormation create stack page, select the IAM resource acknowledgement checkbox and click Create stack.
-
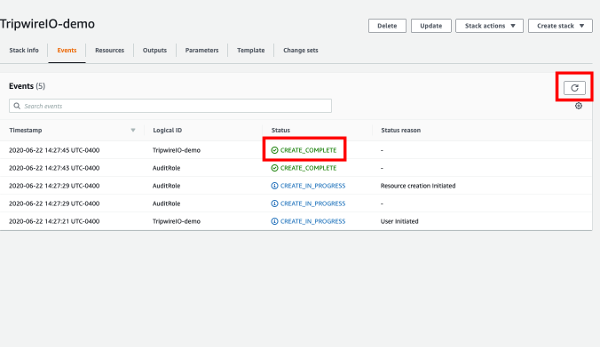
On the newly created stack page in the AWS console, wait until the stack's status is CREATE_COMPLETE.
Tip:
Creating the stack should take less than a minute, but you can refresh the table to update the status.
-
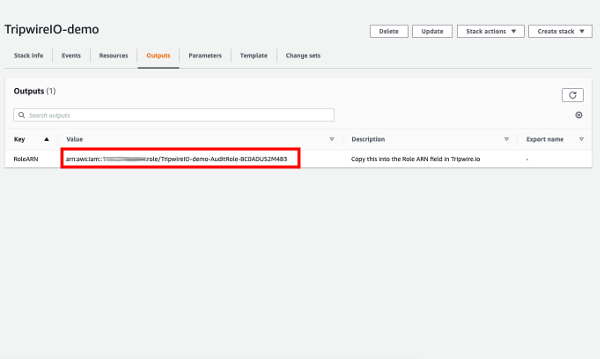
Once the stack is created, click the Outputs tab.
-
Select the value of RoleARN and copy it to the clipboard.
-
Back in Configuration Manager, paste the copied value into the Role ARN (not EKS Role ARN) field.
- Next configure the user to monitor EKS by doing one of the following:
- mapping the user to a Kubernetes role inside the cluster (follow the steps under To add an IAM user or role to an Amazon EKS cluster, using the Role ARN from above).
- granting the user the ability to assume an IAM role that is already mapped to a Kubernetes role in the cluster. If you use this approach, you must enter the EKS Role ARN when creating the Cloud Account.
- Once you have configured EKS, complete the Cloud Account in Configuration Manager.
- Enter the EKS Cluster Name and EKS Role ARN (if necessary).
Click Save to create the new Cloud Account.